HSE Scientists Create Imperceptible but Robust Digital Watermark

HSE scientists have developed an algorithm to protect digital images, significantly enhancing the security of multimedia data on the internet. The algorithm embeds watermarks into images; these watermarks are invisible to the human eye and capable of resisting various attacks. The results of the study have been published in Computers and Electrical Engineering.
With the rise of the internet and social and neural networks, copyright protection for digital content has increasingly presented a challenge. Publishing images online makes them vulnerable to illegal copying and distribution, while visible watermarks are often cropped out or removed. An effective method for protecting images is a watermarking technology that embeds an identifier into an image, and while imperceptible to the human eye, the watermark can be extracted as needed to prove authorship and ownership.
Anna Melman and Oleg Evsyutin at the Department of Cyber Physical Systems Information Security of MIEM HSE have proposed a new algorithm for creating a digital watermark, consisting of several stages. First, the image is divided into 8×8-pixel blocks, and a discrete cosine transform (DCT) is applied to each block. The algorithm converts pixel values into a frequency spectrum, allowing it to highlight important image features and separate them from noise. The watermark is then embedded by modifying the coefficients in the mid-frequency area of the block so that the sum of the absolute values of one half of the coefficients becomes either greater or less than the sum of the absolute values of the other half, depending on the bit of information being embedded.
Imagine a watermarked image as a large cabinet filled with shelves of books (pixels), each with differently coloured covers, arranged in a chaotic order. The algorithm sorts the books by the brightness of their covers, arranging them from the brightest to the dimmest. Then it embeds the required watermark into the cabinet. The logic behind the embedding is as follows: the books on the central shelf (mid-frequency area of the block) get rearranged so that the brightness of the covers on one half of the shelf becomes either greater or less than the brightness of the covers on the other half. The books are swapped depending on whether 0 or 1 is embedded. The changes are so minor that they are imperceptible to the human eye. However, the algorithm can discern changes in the arrangement of books on the central shelf and extract the embedded information accordingly.
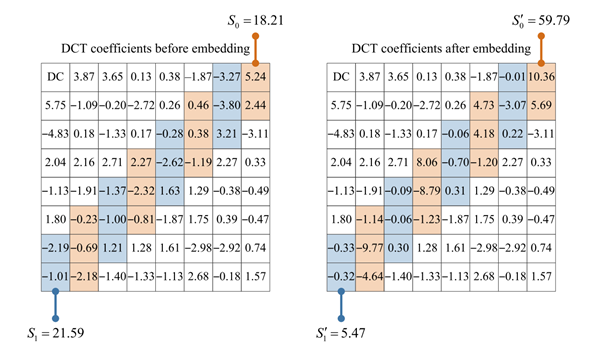
The main advantage of the method lies in achieving a balance between the imperceptibility and robustness of the watermark, facilitated by a modern optimisation algorithm known as the gradient-based optimiser (GBO). GBO is used to determine a vector of coefficient changes that minimises image distortion while maximising the robustness of the watermark. This optimiser combines the advantages of gradient methods and metaheuristic approaches, offering a fast and effective solution to the problem. Unlike other methods, GBO uses the gradient search rule and a local escaping operator, enabling it to circumvent local minima and discover more precise solutions.
'We have devised a method to embed information that minimally distorts the image while also offering high resistance to typical attacks such as compression, changes in brightness, contrast adjustments, cropping, and others,' according to Oleg Evsyutin, one of the study authors.

Экспериментальные результаты показали высокую эффективность предложенного алгоритма по таким показателям, как незаметность и устойчивость к атакам. В частности, водяной знак оставался видимым даже после изменения яркости и контраста, а также применения различных фильтров.

'Our work offers new opportunities for protecting digital images, particularly in circumstances where maintaining high image quality is crucial for online publication,' notes Anna Melman.
The researchers plan to explore the possibilities of applying the algorithm to various types of digital data and usage conditions. In the future, such methods could serve as the foundation for developing robust copyright protection systems on the internet, ensuring the security and integrity of digital content.
© 2024 Elsevier Ltd. All rights reserved. Reprinted from Computers and Electrical Engineering, Vol. 117, 2024, pp. 109271, Anna Melman, Oleg Evsutin, “Image watermarking based on a ratio of DCT coefficient sums using a gradient-based optimizer”.


